Deceptive HR Emails: Sophisticated Phishing Campaign Targets Employees with Fake Policy Updates

Cybersecurity firm Kaspersky has uncovered an advanced phishing operation exploiting corporate trust by disguising malicious emails as HR policy updates. The campaign is notable for its highly personalized approach, including tailored attachments and deceptive visuals, all aimed at harvesting employee email credentials.

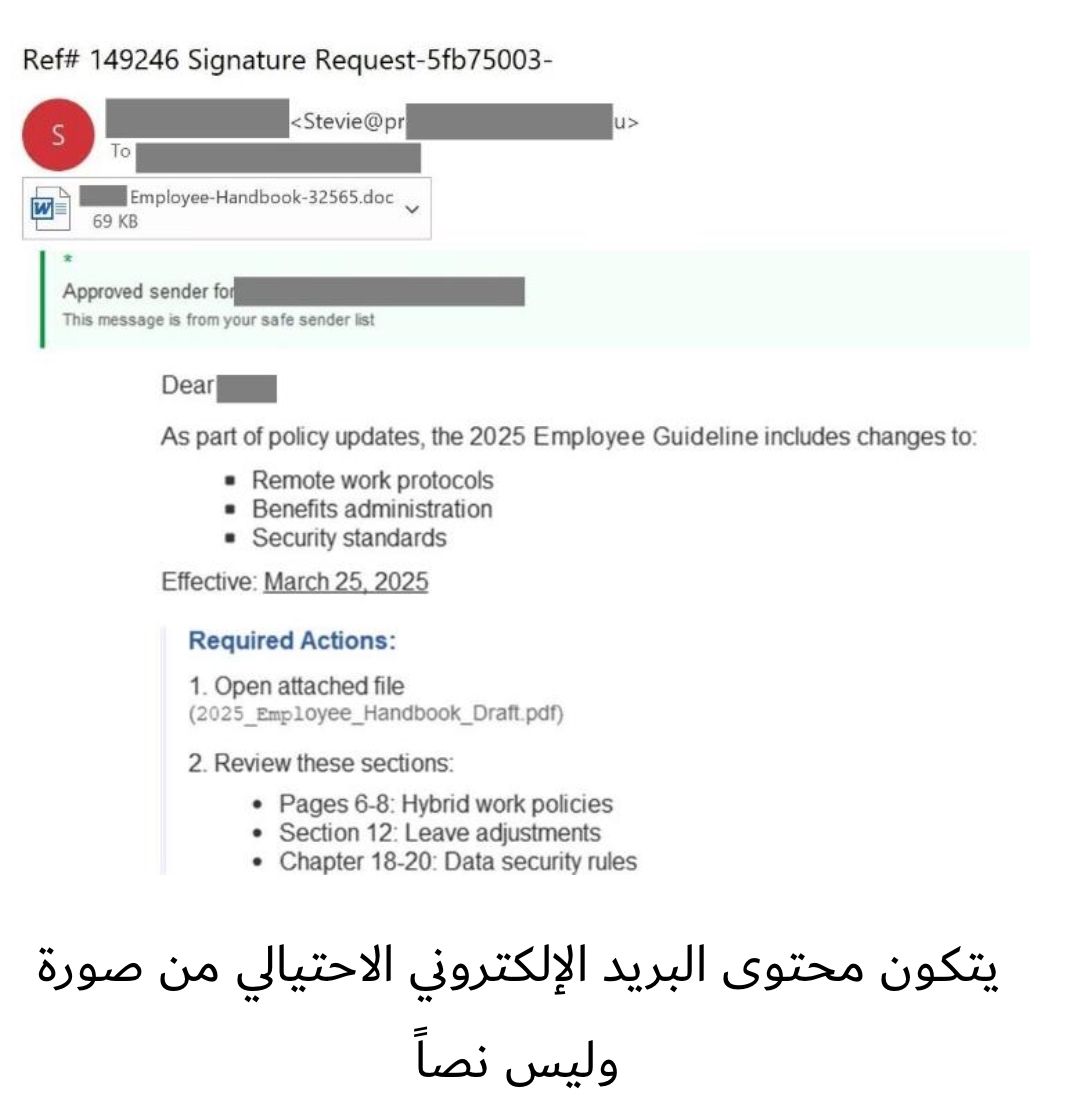
Attackers sent emails featuring the target’s name, a fake "verified sender" badge, and an invitation to review updated remote work policies and security guidelines. However, the email body was not actual text but a single image — a deliberate tactic to evade spam filters.
The attached file, posing as an updated “Employee Handbook,” includes the employee’s name across multiple sections to reinforce authenticity. It presents a table of contents with supposed changes marked in red, followed by a page containing a QR code. Victims who scan the code are directed to a fake login page designed to capture their corporate credentials.
Roman Dedenok, Anti-Spam Expert at Kaspersky, warned, “This campaign demonstrates a new level of phishing sophistication. We may be witnessing a mailing automation system that creates unique email images and attachments per recipient — a method that helps bypass traditional defenses while scaling the attack.”
Kaspersky’s Recommendations for Organizations:
Deploy advanced security solutions on mail servers to detect phishing.
Protect all employee devices, including smartphones, with reliable security software.
Conduct ongoing training on modern phishing tactics.
Urge staff to verify HR communications and watch for signs such as image-based emails or inconsistent document metadata.
